Microsoft Graph PowerShell Connection
The Microsoft Graph PowerShell module is a handy tool that provides a set of cmdlets to interact with Microsoft’s powerful Graph API directly from PowerShell. This enables users to automate and manage resources across a variety of Microsoft services like Office 365, Azure Active Directory, and more.
Module Installation
I am going to show you how to install the module quickly and get access to it.
Install-Module Microsoft.Graph -Scope CurrentUser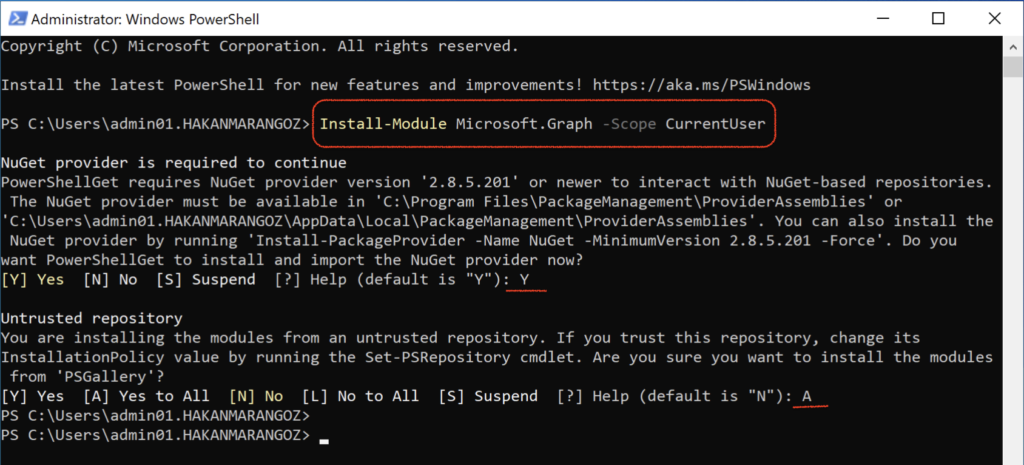
To install the beta module, execute the following command:
Install-Module Microsoft.Graph.Beta -Scope CurrentUser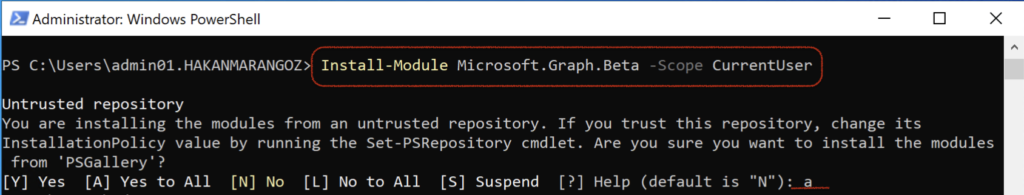
Once the installation is done, you can check the version with this command.
Get-InstalledModule Microsoft.Graph
Get-InstalledModule Microsoft.Graph.Beta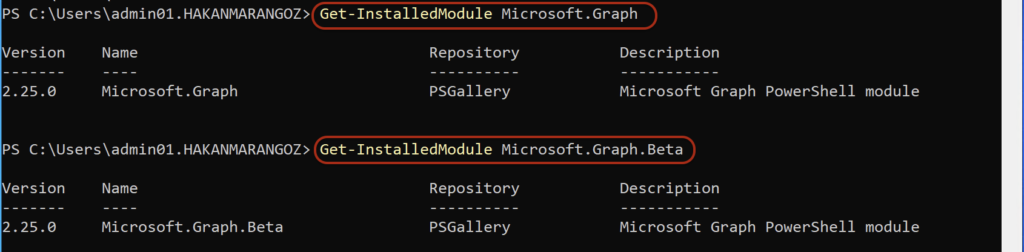
If you have already installed a version of the Microsoft Graph and would like to update it to the latest version, please update the version to the latest with this command.
Update-Module Microsoft.GraphIf you would like to uninstall the Microsoft Graph and dependencies with the module, execute the following command.
Uninstall-Module Microsoft.Graph -AllVersions
Get-InstalledModule Microsoft.Graph.* | ? Name -ne "Microsoft.Graph.Authentication" | Uninstall-Module -AllVersions
Uninstall-Module Microsoft.Graph.Authentication -AllVersionsAuthentication
The PowerShell supports two types of authentication: delegated access, and app-only access. In this guide, we’ll use both;
- Delegated access to sign in as a user, grant consent to the SDK to act on your behalf, and call the Microsoft Graph
- App-only access for unattended scenarios.
Determine required permission scopes
Each API in the Microsoft Graph is protected by one or more permission scopes. The user logging in must grant consent to one of the required scopes for the APIs you intend to utilize. In this example, we will utilize the following APIs:
- List users to find the user ID of the logged-in user.
- List joinedTeams to get the Teams the user is a member of.
- List channels to get the channels in a Team.
- Send message to send a message to a Team’s channel.
The User.Read.All permission scope will enable the first two calls, and the Group.ReadWrite.All scope will enable the rest. These permissions require an account with the Application Administrator or Cloud Application Administrator role to grant consent. For more information, see Microsoft Entra built-in roles.
Using Find-MgGraphCommand to find required permissions
The Find-MgGraphCommand cmdlet can be used to discover the required permissions for another cmdlet. For example, to see all permissions that can be used to call Get-MgUser run;
Find-MgGraphCommand -command Get-MgUser | Select -First 1 -ExpandProperty Permissions
Let’s try to connect to both options as an example.
Option 1: Delegated access to sign in as a user, grant consent to the SDK to act on your behalf, and call the Microsoft Graph
To sign in with the necessary scopes, use the Connect-MgGraph command. You’ll need to use an admin account to give permission for the required scopes.
Connect-MgGraph -Scopes "User.Read.All","Group.ReadWrite.All"The command will take you to a web page where you can sign in using your credentials. Once you’ve done that, the command will show you a message saying Welcome To Microsoft Graph! You only need to sign in once per session.

Option 2: App-only access for unattended scenarios.
You can also use app permissions to grant direct access to the application, which does not require a user to be signed in. These permissions are often used for background services or daemon apps that need full access.
To interact with Microsoft Graph services via APIs, you must register an application in Entra ID and configure the required permissions.
2.1- Register the Entra ID Application:
- Log into the Microsoft Entra Admin Center
- Go to Applications > App Registrations
- Click “New Registration” and mention the name of the app and click “Register”
2.2- Create a Client Secret:
- Go to the “Certificates & secrets” under the app which we created
- Select Client Secrets and click “New client secret” and mention the expiry date and click “Add”
- Keep the secret key securely, once you refresh the page, secret key will be masked on the page.
2.3- Configure Required Api Permissions:
- Go to “API permissions”
- Click “Add a permission > Microsoft Graph
- Add the required “Application permissions” based on your requirement (If you do not the required API permission, please have a look to : Determine required permission scopes line)
- User.Read.All
- Group.ReadWrite.All
You will need Client Secret, Client ID and Tenant ID for authentication (You can find this info under the “Overview” page of the created app registration)
#Configuration
$ClientId = "9c7f8717-29ec-4bc1-b205-682766768ae8"
$TenantId = "3e6a6897-2a7b-405e-9b1d-132e11e17f4d"
$SecretKey = "RpQ8Q~~RR4~W3Q4t8avhnTuFdx0THQ40.SiqLapk"
$SecretKeyString = ConvertTo-SecureString -String $SecretKey -AsPlainText -Force
$ClientSecretCredential = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList $ClientId, $SecretKeyString
Connect-MgGraph -TenantId $tenantID -ClientSecretCredential $ClientSecretCredentialRun the PowerShell script.

You are connected!
